TechNet網路技術: Linux Firewall
摘自: Netfilter Packet Flow https://commons.wikimedia.org/wiki/File:Netfilter-packet-flow.svg
How to list and delete iptables Firewall rules
Firewall通常是企業網路的安全中心,會佈建在企業網路的關鍵位置上,所以如果Firewall本身被Cracker入侵了,那麼Cracker就可以從防火牆主機上直接攻擊DMZ或是企業內部的主機
(1) 網路攻擊: 如果攻擊者的目的只是要癱瘓某企業,那麼極有可能採用DoS或DDoS攻擊(ping-to-death)
(2) 系統入侵: 有一個很重要的觀念一定要牢記”千萬不要為了節省經費而將對外的服務裝在Firewall上”,必須要了解”如果一部主機(不管其安裝甚麼OS)直接放在Internet上,其在不開放任何網路服務的情況下,這部主機無論如何是不可能遭到入侵的”而主機之所以會遭到入侵一定是具備兩項條件:
(1) 這部主機一定有提供某些服務
(2) 其二是這些服務本身就有安全性的瑕疵
(3) Inbound/Outbound的考量: 對於防火牆本機的進出入連線必須嚴格的管控
Defense in Depth動畫: http://www.infosec.gov.hk/public/flash/Defense_in_Depth/Defense_in_Depth.swf
iptables is a firewall that plays an essential role in network security for most Linux systems. While many iptables tutorials will teach you how to create firewall rules to secure your server, this one will focus on a different aspect of firewall management: listing and deleting rules.
In this tutorial, we will
cover how to do the following iptables tasks:
· List rules
· Clear Packet and Byte Counters
· Delete rules
· Flush chains (delete all rules in
a chain)
· Flush all chains and tables,
delete all chains, and accept all traffic
iptables debug trace:iptables 追蹤packet流向的方法,
kernel和module需開啟和build-in相關的config和module,
所以只需要在iptables裡加入trace就可以馬上用。
#
for IPv4
# iptables
-t raw -A OUTPUT -p icmp -j TRACE
# iptables
-t raw -A PREROUTING -p icmp -j TRACE
DMZ
針對不同資源提供不同安全級別的保護,可以考慮構建一個叫做“Demilitarized Zone”(DMZ)的區域。DMZ可以理解爲一個不同于外網或內網的特殊網絡區域。DMZ內通常放置一些不含機密信息的公用服務器,比如Web、Mail、FTP等。這樣來自外網的訪問者可以訪問DMZ中的服務,但不可能接觸到存放在內網中的公司機密或私人信息等。即使DMZ中服務器受到破壞,也不會對內網中的機密信息造成影響。
1. Cisco Design
CCNA
Security Chapter 14
By default, if two interfaces are
both at the exact same security level, traffic is not allowed between those two
interfaces. Also by default the ASA does not like to (meaning it will not)
receive a packet on a specific interface and route the same packet out of the
exact same interface (hairpin routing). You can change both of these default
behaviors
Linux iptables建構DMZ:
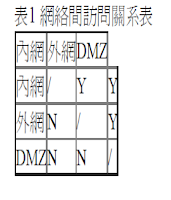
Linux從2.4內核開始,正式使用iptables來代替以前的ipfwadm和ipchains,實現管理Linux的包過濾功能。Linux的包過濾通過一個叫netfilter的內核部件來實現。netfilter內建了三個表,其中默認表Filter中又包括3個規則鏈,分別是負責外界流入網絡接口的數據過濾的INPUT鏈、負責對網絡接口輸出的數據進行過濾的OUTPUT鏈,以及負責在網絡接口之間轉發數據過濾的FORWARD鏈。要構建一個帶DMZ的防火牆,需要利用對這些鏈的設定完成。首先要對從連接外部網絡的網卡(eth0)上流入的數據進行判斷,這是在INPUT鏈上完成。如果數據的目標地址屬于DMZ網段,就要將數據轉發到連接DMZ網絡的網卡(eth1)上;如果是內部網絡的地址,就要將數據轉發到連接內部網絡的網卡(eth2)上。表1顯示了各個網絡之間的訪問關系。
根據表1,可以明確以下六條訪問控制策略。
1.內網可以訪問外網
內網的用戶顯然需要自由地訪問外網。在這一策略中,防火牆需要進行源地址轉換。
2.內網可以訪問DMZ
此策略是爲了方便內網用戶使用和管理DMZ中的服務器。
3.外網不能訪問內網
很顯然,內網中存放的是公司內部數據,這些數據不允許外網的用戶進行訪問。
DMZ中的服務器本身就是要給外界提供服務的,所以外網必須可以訪問DMZ。同時,外網訪問DMZ需要由防火牆完成對外地址到服務器實際地址的轉換。
5.DMZ不能訪問內網
很明顯,如果違背此策略,則當入侵者攻陷DMZ時,就可以進一步進攻到內網的重要數據。
6.DMZ不能訪問外網
此條策略也有例外,比如DMZ中放置郵件服務器時,就需要訪問外網,否則將不能正常工作。iptables - connection states
~
User-land states | Page Up |
As you have seen, packets may take on several different states within the kernel itself, depending on what protocol we are talking about. However, outside the kernel, we only have the 4 states as described previously. These states can mainly be used in conjunction with the state match which will then be able to match packets based on their current connection tracking state. The valid states are NEW, ESTABLISHED, RELATED and INVALID. The following table will briefly explain each possible state.
Table 7-1. User-land states
| State | Explanation |
|---|---|
| NEW | The NEW state tells us that the packet is the first packet that we see. This means that the first packet that the conntrack module sees, within a specific connection, will be matched. For example, if we see a SYN packet and it is the first packet in a connection that we see, it will match. However, the packet may as well not be a SYN packet and still be considered NEW. This may lead to certain problems in some instances, but it may also be extremely helpful when we need to pick up lost connections from other firewalls, or when a connection has already timed out, but in reality is not closed. |
| ESTABLISHED | The ESTABLISHED state has seen traffic in both directions and will then continuously match those packets. ESTABLISHED connections are fairly easy to understand. The only requirement to get into an ESTABLISHED state is that one host sends a packet, and that it later on gets a reply from the other host. The NEW state will upon receipt of the reply packet to or through the firewall change to the ESTABLISHED state. ICMP reply messages can also be considered as ESTABLISHED, if we created a packet that in turn generated the reply ICMP message. |
| RELATED | The RELATED state is one of the more tricky states. A connection is considered RELATED when it is related to another already ESTABLISHED connection. What this means, is that for a connection to be considered as RELATED, we must first have a connection that is considered ESTABLISHED. The ESTABLISHED connection will then spawn a connection outside of the main connection. The newly spawned connection will then be considered RELATED, if the conntrack module is able to understand that it is RELATED. Some good examples of connections that can be considered as RELATED are the FTP-data connections that are considered RELATED to the FTP control port, and the DCC connections issued through IRC. This could be used to allow ICMP error messages, FTP transfers and DCC's to work properly through the firewall. Do note that most TCP protocols and some UDP protocols that rely on this mechanism are quite complex and send connection information within the payload of the TCP or UDP data segments, and hence require special helper modules to be correctly understood. |
| INVALID | The INVALID state means that the packet can't be identified or that it does not have any state. This may be due to several reasons, such as the system running out of memory or ICMP error messages that do not respond to any known connections. Generally, it is a good idea to DROP everything in this state. |
| UNTRACKED | This is the UNTRACKED state. In brief, if a packet is marked within the raw table with the NOTRACK target, then that packet will show up as UNTRACKED in the state machine. This also means that all RELATED connections will not be seen, so some caution must be taken when dealing with the UNTRACKED connections since the state machine will not be able to see related ICMP messages et cetera. |
These states can be used together with the --state match to match packets based on their connection tracking state. This is what makes the state machine so incredibly strong and efficient for our firewall. Previously, we often had to open up all ports above 1024 to let all traffic back into our local networks again. With the state machine in place this is not necessary any longer, since we can now just open up the firewall for return traffic and not for all kinds of other traffic.


留言
張貼留言